
Document centralization solutions form a core infrastructure for improving collaboration efficiency and strengthening enterprise information management. By centralizing document storage, sharing, search, and version control, organizations gain both operational convenience and stronger governance. At the same time, document centralization solutions are complex systems where servers, clients, networks, and web services intersect, making integrated security management across all essential components.
Security in document centralization environments must therefore begin with a complete understanding of the entire system, rather than enhancement of isolated features. This article examines how SBOM, VEX, and OS hardening reinforce the operational quality, transparency, and credibility of document centralization solutions.
1. The Role of Document Centralization Solution : The Front Line of Preventing Data Leakage and Loss
Document centralization solutions fundamentally strengthen internal information control by forcing users to store data at servers rather than individual PCs. This approach significantly reduces insider-driven data leakage, including risks related to employee turnover—areas that are often difficult to fully control using DRM or DLP alone.
In addition, access rights can be controlled by department, project, and user authority. All activities such as document creation, modification, and external transfer are logged and traceable, enhancing organizational security awareness.
From an external threat perspective, even if a personal PC or NAS is compromised, original documents remain safely stored on the central server.
Version control and recovery features also minimize damage caused by accidental or intentional data loss, ensuring business continuity.
2. The Role of SBOM and VEX : Transparency and Proactive Response to Supply Chain Threats
SBOM and *VEX play critical roles in strengthening supply chain security and vulnerability management within document centralization solutions.
An SBOM records all open-source software, third-party components, libraries, and dependencies included in a system.
By linking SBOM data with the *CVE database, organizations can automatically detect vulnerabilities within specific components.
When vulnerabilities—such as those affecting *OpenSSL—are discovered, affected systems can be quickly identified and patched.
Beyond simple asset tracking, SBOM enables concrete attack surface management by clearly identifying which servers and systems are exposed to known vulnerabilities.
Its importance has grown especially in response to large-scale incidents such as SolarWinds and Log4j, and it is now considered a key tool for regulatory compliance, including the U.S. Executive Order 14028 and the EU Cyber Resilience Act (CRA).
VEX further enhances this process by determining whether identified vulnerabilities actually impact real operating environments. By classifying vulnerabilities as “Affected” or “Not Affected,” VEX allows security teams to prioritize only real risks, enabling efficient use of limited security resources while maintaining system stability.
* VEX(Vulnerability Exploitability eXchange) : A standardized format that determines whether SBOM-listed vulnerabilities pose real security risks.
*CVE: A global standard for identifying known security vulnerabilities
*OpenSSL: A widely used encryption software for securing internet communications
3. The Role of OS Hardening : Strengthening Defense at the Attack Execution Level
*OS Hardening complements SBOM and VEX by strengthening security at the execution layer. Based on the principles of least privilege and minimal exposure, unnecessary services and ports are disabled, access permissions are minimized, and system integrity is regularly verified.
Even if an attack succeeds, OS hardening restricts lateral movement and minimizes damage propagation across servers and endpoints. As such, it serves as the final defensive layer that limits the overall impact of cyber incidents.
* OS Hardening : Security measures that strengthen OS settings to reduce the attack surface and vulnerability exposure
4. Conclusion: An Integrated Security Framework That Strengthens the Reliability of Document Centralization Solutions
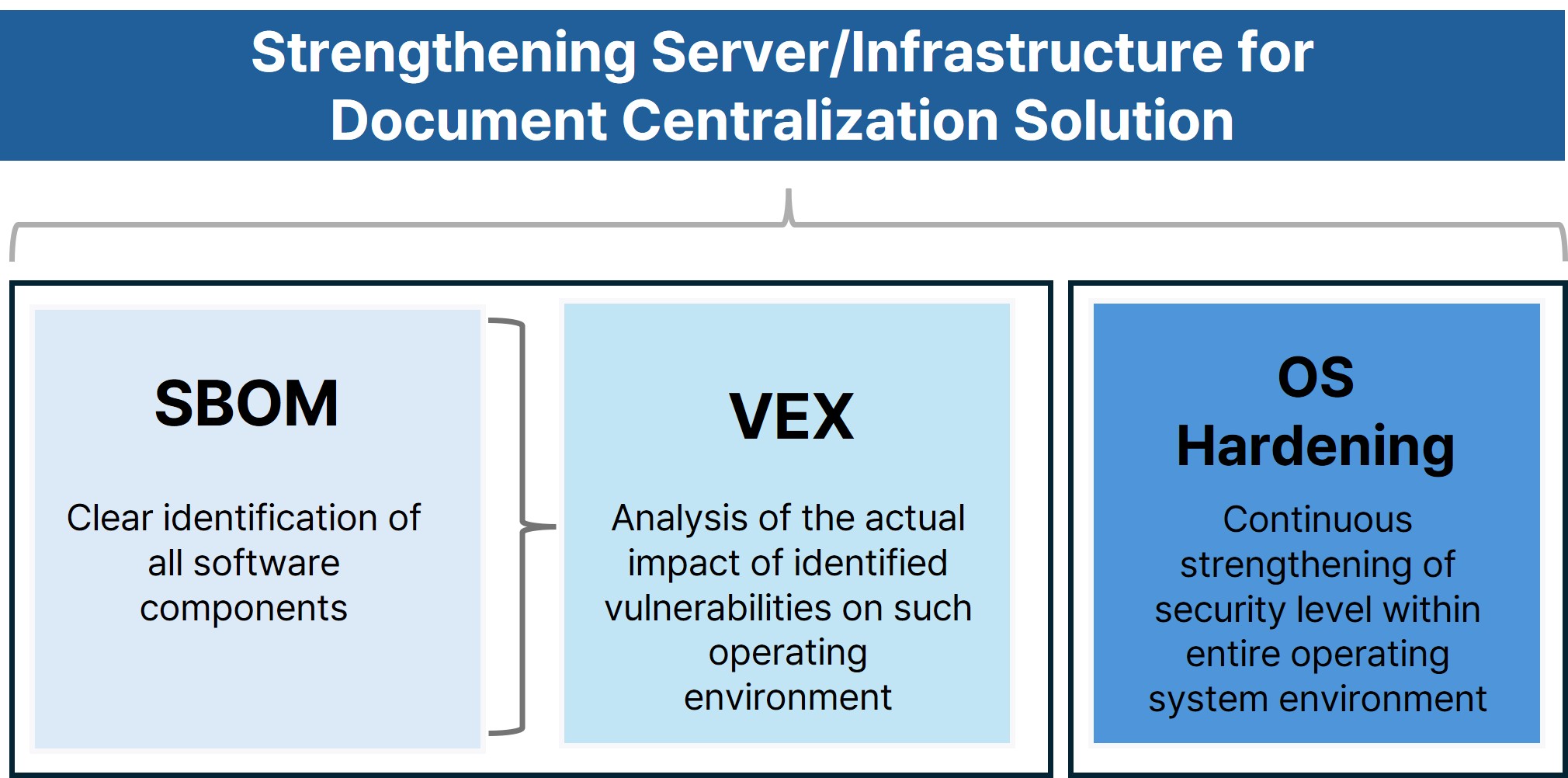
Document centralization solutions have become core infrastructure that protects and manages a company’s critical information. This makes operational stability, transparency, and long-term reliability essential requirements—not optional features.
Improving visibility into system components (SBOM), analyzing the real impact of vulnerabilities (VEX), and continuously strengthening the operating environment (OS Hardening) together form the basis for a more trustworthy and resilient document centralization solution.
To support this direction, Cyberdigm is enhancing SBOM-based component transparency through joint research with Korea University’s CSSA and applying these capabilities across its solutions to further improve system reliability and security.
Ultimately, the security level of a document centralization solution lies in how reliably, transparently, and securely it operates.

 한국어
한국어







