내부 직원에 의한 유출 사건이 끊이지 않고 있습니다.
최근 S바이오로직스 직원이 회사 자료 300장 분량을 무단으로 반출하려다 적발되어 현행범으로 체포되었다는 소식이 전해졌죠.
(출처: http://www.m-i.kr/news/articleView.html?idxno=990583)
이외에도 경쟁사의 직원을 회유하여 고객 정보를 빼돌리게 시켜 기소된 A사,
반도체 관련 장비의 도면을 해외 기업에 팔아 부당한 이익을 취하거나 설계 도면을 빼돌리려던 직원 등
각종 뉴스와 신문을 통해 보도된 내부 유출 사건들이 있습니다.
"기업 내부 정보 유출? 근데 보통 유출은 해커 공격이나 외부 사람들로 인해 발생하지 않나요?"
보통 업무 관련 내용이 유출되는 것은 외부의 공격 때문일 것이라 생각하는 사람들이 많습니다.
하지만 회사 기밀 자료를 유출하는 행위자의 80%가 전현직 임직원이라는 점! (출처: https://www.etnews.com/20220329000125)
직접 업무를 수행하는 인력이다 보니 어떤 일들이 진행되고 있는지, 관련 자료는 어떤 것들이 있는지 파악하고 있기에
내부 인력에 의한 유출은 회사에 더욱 큰 타격이 될 수밖에 없죠..!
마침 작년부터 이어지는 디지털 전환 열풍으로 사이버 위협에 대비하기 위한 보안 솔루션에 대한 수요가 높아지고 있습니다.
파일 암호화 솔루션, 디지털 권한 관리(DRM) 및 데이터 손실 방지(DLP)는 디지털 자산을 보호하기 위해 일반적으로 사용되는 보안 솔루션으로 알려져 있죠.
보안 솔루션들을 보다 구체적으로 비교한 내용이 궁금하다면?
문서중앙화 vs DRM, DLP, VDI 비교. 우리 회사에 딱 맞는 문서 보안 솔루션은?
하지만 각각 솔루션의 단점은 존재 하는데요. DRM의 경우 시스템 성능을 저하시킬 수 있고 암호화 키를 분실하면 데이터에 접근할 수 없어
파일이 있어도 활용할 수 없게 됩니다. 또한 사용할 때마다 암복호화를 진행해야 하기 때문에 사용자의 편의는 기대할 수 없죠.
DLP 또한 민감한 데이터에 접근 하기 위해 복잡한 프로세스를 거쳐야해 사용자 불편이 발생하며, 문서가 유출된 후 후속 조치는 가능하지만
내부자의 문서 유출을 막지는 못한다는 단점이 있습니다.
"그렇다면, 각 솔루션의 단점을 보완해 사용하기 편리하면서 내부자에 의한 문서 유출을 막는 보안 솔루션은 없을까요??"
사이버다임의 문서중앙화로 문서 보안 걱정 한 번에 해결하세요!
【문서중앙화 솔루션이란】
: 업무 산출물들을 중앙 서버 한곳에 모아서 저장하여 문서 보안부터 관리까지 한 번에 해결할 수 있는 솔루션입니다.
아무나 관련 자료를 볼 수 없도록!
6단계로 섬세하게 권한 설정
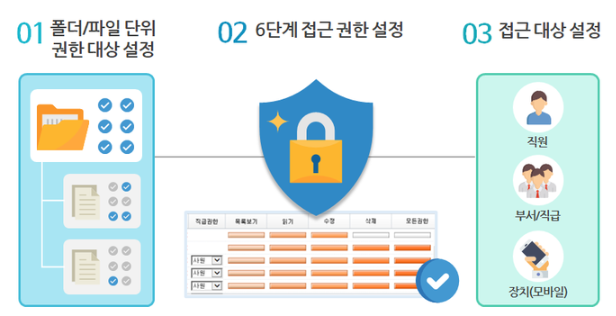
모든 산출물들이 중앙 서버에 모여있으니 효율적인 업무 활용에는 탁월할 것입니다. 하지만 모든 직원들이 문서에 접근할 수 있다면?
문서 보안은 엉망이 되어버리죠. 하지만 사이버다임 문서중앙화 솔루션이 있다면 그런 걱정, 더 이상 하지 않으셔도 됩니다!
섬세하게 문서 접근 권한을 설정할 수 있기 때문이죠. 부서별로 접근 권한을 설정할 수 있을 뿐만 아니라 부서 내에서도
특정 직급 이상만 문서에 대한 권한을 갖도록 설정할 수 있습니다. 그리고 직원 개개인별로, 또는 장치에 따라 접근할 수 있는지 설정할 수 있습니다.
접근할 수 있는 범위도 구체적이죠! 폴더 내 파일의 목록만 볼 수 있거나, 내용 조회만 가능한 읽기, 내용을 변경할 수 있는 수정,
문서를 삭제할 수 있는 삭제, 그리고 모든 권한과 같이 세세하게 권한 범위가 나누어져 있습니다.
마음대로 문서를 출력하지 못하도록
인쇄 제어 보안정책 설정!
서두에 언급한 S바이오로직스 사건 속 직원은 업무 문서들을 출력하여 유출하려 했죠.
문서를 열어 인쇄 버튼만 누르면 쉽게 출력할 수 있기에 출력물 보안도 각별히 신경써야 합니다.
문서중앙화 솔루션에서는 관리자의 승인을 얻어야만 문서를 출력할 수 있도록 보안 정책 설정이 가능합니다!
또한 누가, 언제 문서를 출력한 것인지 워터마크를 표시하여 출력한 사람에 대한 흔적을 출력물에 남길 수 있죠!
인쇄 관련 설정뿐만 아니라 캡처 제어, 로컬 PC 다운로드 가능 여부, 응용프로그램에서 생성되는 산출물 중 어떤 것을 중앙화할 것인지 등
세부적인 요소도 보안 정책으로 설정할 수 있죠.
본인 메일로 유출하면 어떻게 하죠?
웹사이트별 문서 첨부 제어 기능!
"직원들이 업무 파일들을 메일로 유출하면 어떻게 하죠? 직원들의 메일 계정 전체를 확인해 볼 수도 없고 골치 아프네요..."![]()
걱정 마세요! 문서중앙화 솔루션에서는 각기 다른 웹브라우저 메일별로 파일 첨부 가능 여부를 설정할 수 있습니다.
예를 들어, 직원들이 개인 용도로 사용하는 경우가 많은 네이버 메일은 파일을 첨부할 수 없도록 설정하고,
외부 협력사와 소통 시 사용하는 경우가 많은 지메일은 파일 원본 혹은 URL을 통해 메일에 첨부할 수 있도록 설정하는 것이죠.
게다가 관리자가 회사의 상황에 맞게 언제든 변경할 수 있기에 더욱 편리하고 확실하게 보안 기능을 사용할 수 있습니다.
누가 파일을 수정했는지 알 수 있나?
문서 이력 조회에서 확인!
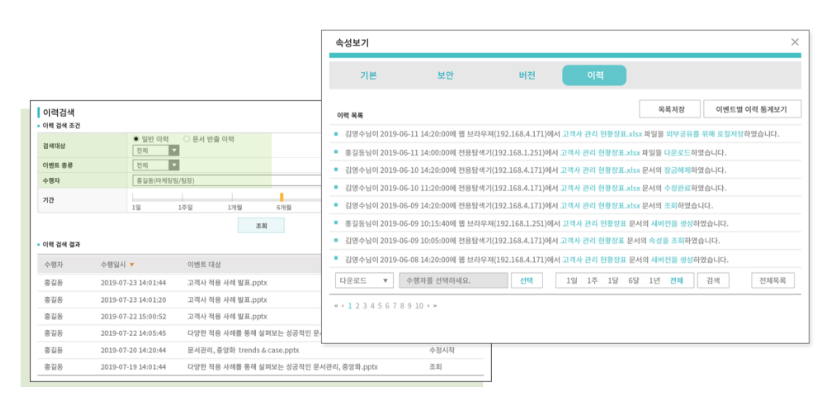
문서가 수정된 최근 날짜는 탐색기의 '수정한 날짜'열에서 확인할 수 있습니다. 그런데 누. 가. 수정했는지 알고 싶은 적 있지 않으신가요?
문서중앙화 솔루션 속 이력 조회 기능은 문서에 대한 모든 활동이 이루어진 날짜와 시간뿐만 아니라 누가, 어떤 행동을 했는지 하나하나 기록하여 보여줍니다.
누가 이 문서를 조회했는지, 수정했는지 뿐만 아니라 저장 위치를 어느 폴더로 이동하였는지, 배포 URL을 생성하였는지, 잠겨있던 파일을 잠금 해제하였는지,
새 버전을 생성하였는지, 속성을 조회하였는지 등 세세하게 확인할 수 있기에 중요 문서들의 보안 관리를 더욱 철저하게 할 수 있겠죠?
사이버다임 문서중앙화 솔루션으로 내부 문서 유출을 막을 수 있었던 고객사 이야기가 궁금하다면?
▶ [고객사 인터뷰] 현대카드, 사이버다임 문서중앙화 솔루션으로 <개인정보 문서 보안 관리> 문서 유출 원천 차단.
▶ [고객사 인터뷰] 디자인그룹 희오 "프로젝트 작업물 유출 방지-체계적인 문서관리- 재택근무" 팔방미인 문서중앙화 솔루션 cloudium.
---------------------------------------------------------------------------------
문서중앙화 솔루션으로 내부 문서 유출을 방지하는 방법~ 다들 잘 보셨나요?
사이버다임 문서중앙화는 총 세 가지 종류가 있는데요!
고객의 환경에 맞게 유연한 커스터마이징을 할 수 있는 Destiny ECM
서버를 관리할 수 있는 내부 It 관리 인원이 있고 하드웨어와 소프트웨어를 구매해 소유 후 관리할 수 있는 클라우디움 구축형
소규모 사용자나 사용 용량이 작아 월 비용을 내고 서버를 임대해 사용할 수 있는 클라우디움 과금형

 한국어
한국어







