사회 전반에 디지털이 도입되면서 사이버 위협에 관한 뉴스들이 빈번해지고 있는 가운데,
특히 랜섬웨어에 대한 소식들이 끊이지 않고 있습니다.
랜섬웨어가 뭔지 다들 알고 계신가요?
"랜섬웨어? pc가 감염된다는 말은 들었는데 정확하게는 모르겠어요!"
-----------------------------------------------------------------------------------
【랜섬웨어】
: 컴퓨터 사용자의 파일들을 암호화하여 금전을 요구하는 악성코드
즉, 사용자의 PC를 장악하거나 데이터를 암호화한 후, 정상적으로 되돌리길 원한다면 대가로 금전을 요구하는 악성코드입니다.
몸값이라는 의미의 Ransom과 소프트웨어 Software를 합쳐 랜섬웨어(Ransomware)라는 단어가 나왔다 생각하시면 좀 더 쉽게 이해할 수 있죠!
사이버 보안 관련하여 랜섬웨어는 무시할 수 없는 존재입니다. 그렇기에 사이버다임 블로그에서도 이를 주제로 여러 번 게시물이 업로드되었죠.
하지만 해를 거듭할 수 록 랜섬웨어의 공격은 줄어드는 게 아니라 오히려 더욱 다양하고 강력해지고 있습니다.
최근 트렌드마이크로에서 발표한 '2022 상반기 보안 위협 보고서'에 따르자면,
올해 상반기가 작년 동기에 비해 1) 랜섬웨어를 탐지한 횟수가 2배가 늘었고 2) 주요 랜섬웨어는 전년 대비 500%나 증가했다고 합니다.
(출처: https://www.boannews.com/media/view.asp?idx=109644)
얼마 전, 모 백신 프로그램도 새로운 악성 프로그램을 블랙리스트에 추가하기 위한 업데이트를 진행하다 오탐지로 인해 문제가 생겼었죠..!
(◾블랙리스트: PC나 모바일에 출입할 수 있는 악성 프로그램을 사전에 차단하기 위해 접근 불가한 프로그램을 등록하는 것)
심지어 해커가 주문자의 의뢰를 받아 대신 제작하는 서비스형 랜섬웨어도 급증하고 있습니다.
본인 실력이 뛰어나지 않더라도 서비스형 해킹 툴을 통해 사이버 공격에 뛰어들고,
공격자들은 제작에 그치는 것이 아니라 고객 서비스와 만족도 조사까지 하며 점점 조직화되고 있다 합니다.
랜섬웨어 공격에도 문서 보안이 가능한 솔루션이 사이버다임 문서중앙화 입니다!

모든 프로그램이 접근 가능? NO! 승인된 프로그램만 접근 가능!
다들 업무 산출물, 즉 문서들을 어디에 저장하시나요? 대부분 개인 PC에 저장하고 계실 겁니다.
랜섬웨어는 보통 사용자 PC 감염을 시작으로 서버 스토리지에 번진다는 양상을 보이는데요.
개인 PC에 문서를 저장하는 것이 보안 차원에서 안전한 방법은 전혀 아니죠. 반면, 문서중앙화는 모든 산출물을 중앙 서버에 저장합니다.
그렇기에 문서들이 저장되어 있는 중앙 서버만 안전하게 지키면 됩니다!
"근데 중앙 서버가 공격당하면 큰일인 거 아닌가요?"
걱정 마세요, 아무 프로그램이나 접근할 수 없습니다!
중앙 서버에 저장된 문서를 작업할 때는 사용자의 로컬 PC에 가상 보안 영역인 샌드박스를 생성합니다.
그리고 화이트리스트(Whitelist) 방식을 사용해 접근 가능한 프로그램들만 접근할 수 있죠.
그렇기 때문에 악성 프로그램처럼 허용되지 않은 프로그램들은 서버에 접근이 아예 불가합니다!
악성 프로그램에 접근할 수 없도록! 샌드박스를 통해 작업!
"요즘 랜섬웨어들 중엔 화이트리스트 방식이 소용없는 경우도 있다는데요. 그러면 꼼짝없이 당하는 거 아닌가요?"
'파일리스형 매그니베르 랜섬웨어'가 바로 화이트리스트 방식이 통하지 않는 랜섬웨어 중 하나입니다.
프로그램 자체가 없기에 허용된 프로그램만 승인하는 화이트리스트 방식이 소용없는 것이죠.
2018년에 사이버다임의 고객사 중에도 파일리스형 매그니베르 랜섬웨어 공격을 받은 사례가 있는데요!
‘파일리스형 변종 랜섬웨어’, 화이트리스트로 못 막아 - 데일리시큐
막강한 파일리스형 매그니베르 공격에도 큰 문제가 생기지 않았던 이유는 바로! 작업 시, 서버에 저장된 원본을 직접 수정하는 방식이 아니기 때문이죠!
사이버다임 문서중앙화 솔루션은 중앙 서버에 저장된 문서를 작업할 때, 1) 가상 보안 영역인 샌드박스를 생성하여 작업하며
2) 원본 파일을 직접 수정하는 것이 아니라 프록시 파일을 수정한 뒤 서버에 업로드합니다.
최신 랜섬웨어라도 서버 속 원본 파일을 직접 작업할 수는 없으니 중앙 서버에 저장된 문서들을 완벽하게 보호할 수 있죠!
여기서 잠깐! 프록시 파일이란?
프록시 파일(Proxy File)은 서버에 저장된 원본 파일을 대신하는 가상 파일을 말합니다.
만약 감염이 된다면? 버전 관리를 통해 손쉽게 복구!
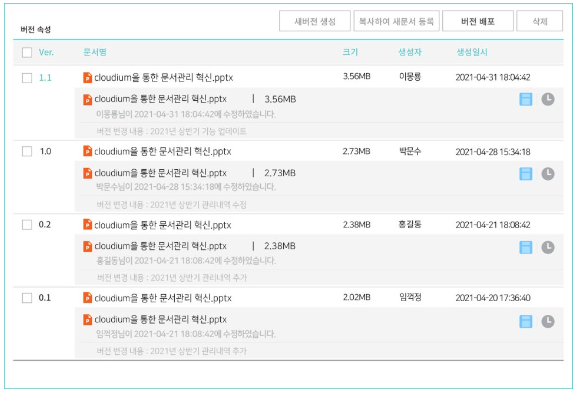
"그럼 만~약에 랜섬웨어가 샌드박스 영역에서 작업하던 문서를 감염시키면요?"
위에서 서버 속 문서를 작업할 때 가상 영역에서 프록시 파일로 수정한 뒤 서버에 업로드한다는 내용을 말씀드렸는데요.
이때 작업한 문서는 새로운 버전의 문서로 저장됩니다. 그렇기에 랜섬웨어에 감염된 문서는 삭제하고 버전 관리 기능으로 이전 버전 파일을 복구하면 해결 완료!
버전 관리 기능은 가장 최신 작업본을 확인하거나 과거 기록을 다시 한번 보고 싶을 때와 같이 문서 기록 관리에 있어 필요한 기능인 줄 알았는데
이렇게 파일 복구로도 사용할 수 있다니! 정말 대단하지 않나요!
-----------------------------------------------------------------------------------------
점점 강해지는 랜섬웨어의 기세에도 끄떡없는 사이버다임 문서중앙화 솔루션의 특징에 대해 알아보았습니다.
보다 안전한 업무 환경을 위해, 소중한 회사 자산인 문서 보안을 위해 사이버다임 문서중앙화가 함께 하겠습니다
고객의 환경에 맞게 유연한 커스터마이징을 원하는 분들에게 Destiny ECM
서버를 관리할 수 있는 내부 IT 관리 인원이 있고 하드웨어와 소프트웨어를 구매해 소유 후 관리하길 원한다면 클라우디움 구축형
소규모 사용자나 사용 용량이 작아 월 비용을 내고 서버를 임대해 사용하길 원한다면 클라우디움 과금형

 한국어
한국어











